
A Fix Is Long Overdue for One of the Most Extensive, Yet Lesser-Known Surveillance Risks of Our Age: the Technical Vulnerabilities at the Heart of the World’s Mobile Communications Networks.
We’ve all been there before: You’re traveling abroad, and as your plane lands and is taxiing to the gate, you reach for your phone, wait for it to connect to the local network, and then you are greeted with a text message: “Welcome abroad, you’re now roaming!” Beyond the exorbitant fees, few of us are likely to give the matter much thought.
However, hidden within this seemingly routine transaction lies one of the most extensive, yet lesser-known surveillance risks of our age: the technical vulnerabilities at the heart of the world’s mobile communications networks. Accompanying the complex arrangement of global networks, international roaming service providers, and financial agreements are surveillance actors who access and covertly manipulate decades-old protocols to extract your sensitive personal information from the mobile network. Human rights and national security risks abound. A new report by the Citizen Lab (a research center with which we are affiliated) details how it all works.
Telecommunications companies constantly exchange huge volumes of messages using a private global network to “signal” when users attempt to roam and use services on partner networks in virtually any country around the world. This private network, called the IP Exchange (IPX), was originally conceived to provide a single connection from one mobile network to other partner networks to facilitate the transport of signaling messages needed for ubiquitous international roaming. Because these signaling messages provide essential user authentication, registration, and service information, they also allow telecommunications companies to retrieve extraordinarily detailed information about a user, including whether a phone number is active, which services are available to them, to which network the phone is currently connected, and most importantly, where they are geolocated at any time relative to the multitude of cell towers to which they connect as they traverse a city.
While at one time this information was restricted to a relatively small club of mobile telecommunications companies, membership has since diversified to private companies selling geolocation surveillance services. Some of these entities gain access to these highly sensitive signaling protocols by buying entry into the club from country network operators seeking more profit—such as small Caribbean, Asia-Pacific, eastern European, and African-based telecommunications firms as revealed in a 2020 article by the Guardian. In other cases, telecommunications firms are compelled by their country’s government to integrate a vendor’s software system into country networks to become an element of their surveillance apparatus—allowing that vendor to access the location and communications of domestic users or those using other country networks connected to the IPX.
Once inside the club, these private surveillance vendors have free rein to act as a telecommunications firm to exchange the same signaling messages but exploit this access to covertly track individuals, disrupt their cell phone services, or even intercept their text messages and voice calls. The surveillance vendors then sell the data and access to government law enforcement or security services. Figure 1 shows how a surveillance actor who enters into financial agreements with mobile network operators and an IPX network provider can acquire the routing addresses and access needed, acting as a roaming partner network, but to surveil users on unprotected networks.
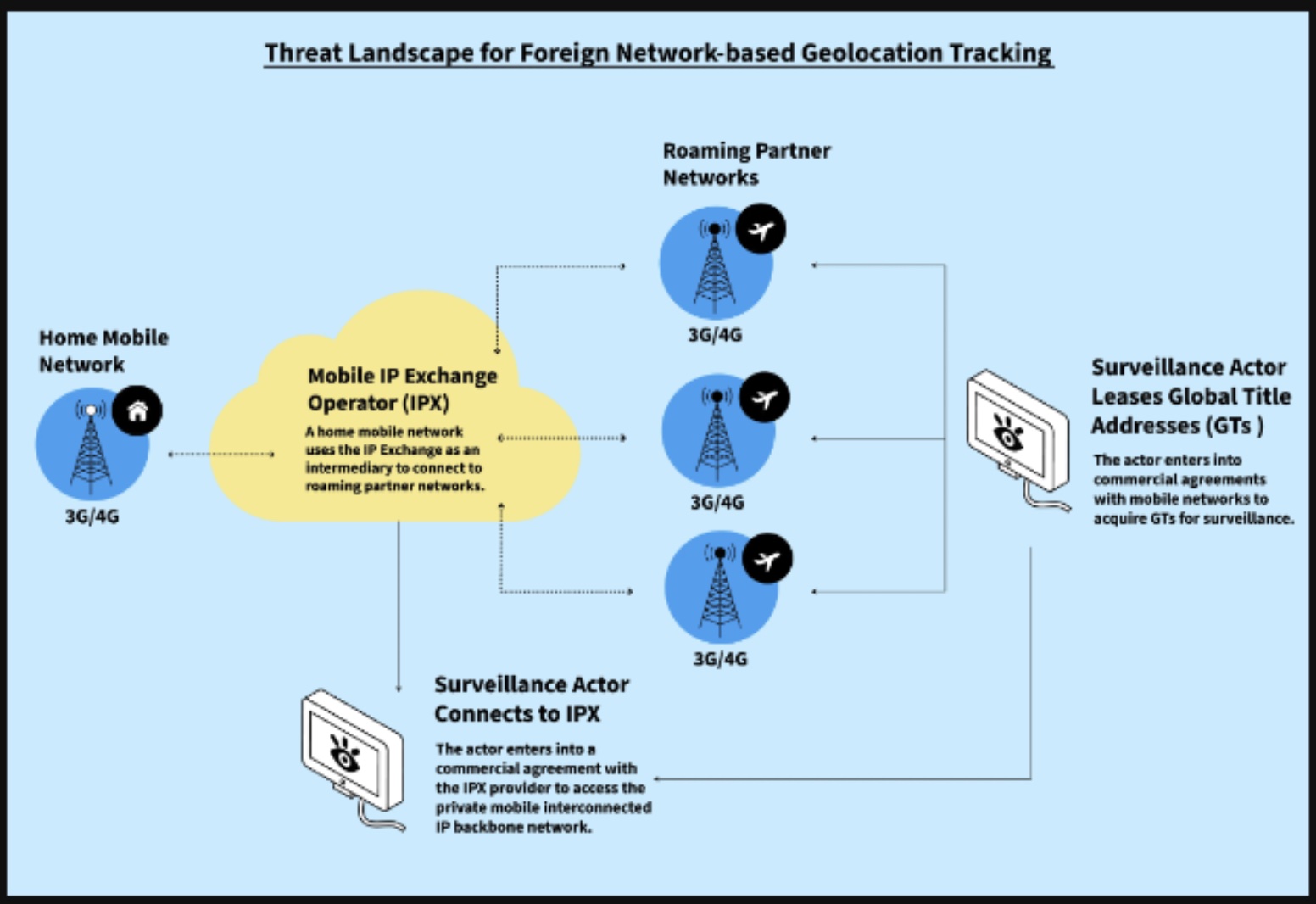
Moreover, this surveillance capability is not limited to older 3G technologies. The surveillance techniques that have been available to exploit 3G networks for 20 years are also widely used in 4G and 5G networks. Sophisticated surveillance firms often use techniques that involve equivalent signaling messages concurrently on all three network types to trick a targeted network into sending them your location information. Naturally, governments are eager consumers of such services, especially those that lack their own sophisticated signals intelligence capabilities. Why spend money building your own National Security Agency (NSA)-style surveillance system when you can simply buy one off the shelf?
Providing these types of tracking abilities to law enforcement or security agencies, many of whom have terrible human rights records and are implicated in acts of domestic and transnational repression, is a recipe for abuses, abductions, and even murder.
The kinds of geolocation tracking capabilities offered by these surveillance firms is different from mercenary spyware, which involves covert penetration of a target’s mobile device. Spyware is malicious software implanted surreptitiously on a target’s device, while geolocation tracking involves exploiting systems that operate at a network layer. Although spyware is far more intrusive and has received considerable media attention in recent years, the harms caused by the industries are very similar. And as with the market for mercenary spyware, the absence of regulations around these types of tracking abilities is enabling transnational repression and authoritarian practices to spread widely.
How bad is it? Based on attack data from security firewalls shown in the Citizen Lab report, the volume of malicious surveillance attempts is staggering. We observed over 13 million confirmed surveillance attempts targeting African countries from more than 375 networks in 2023 alone. Although it is impossible to say exactly who is targeting whom in each of these instances, surveillance attempts using signaling protocols, as defined by mobile industry standard working groups, such as the GSM Association, are almost certainly malicious and not part of normal roaming operations.
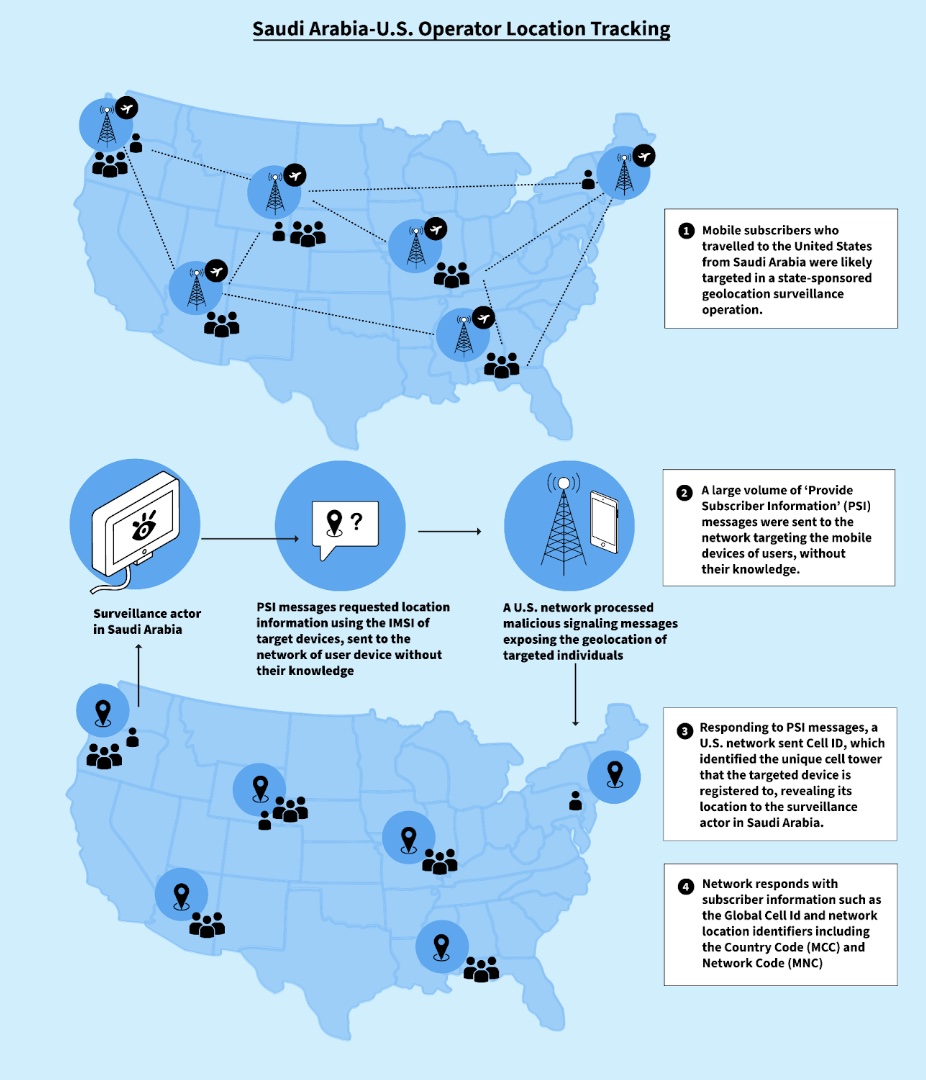
We also observed numerous requests sent from networks in Saudi Arabia to geolocate the phones of Saudi users as they were traveling in the United States. Millions of these requests targeting the international mobile subscriber identity (IMSI), a number that identifies a unique user on a mobile network, were sent over several months, and several times per hour on a daily basis to each individual user. Saudi Arabia is one of the world’s most aggressive countries with respect to transnational repression, and Riyadh has been implicated in the harassment, physical assault, and murder of Saudi dissidents abroad. Such geolocation information could obviously be very helpful in those efforts.
Since the sector is almost entirely unregulated, yet highly profitable, surveillance vendors are spreading their capabilities far and wide. In a 2020 Citizen Lab report, we discovered the services of just one vendor, Circles, was being supplied to government clients with highly concerning human rights records, including Botswana, Chile, Ecuador, El Salvador, Equatorial Guinea, Guatemala, Honduras, Indonesia, Kenya, Malaysia, Mexico, Morocco, Nigeria, Peru, Serbia, Thailand, the United Arab Emirates (UAE), Vietnam, Zambia, and Zimbabwe.
This simple geolocation tracking ability can have lethal consequences. A recent investigation published by Haaretz discovered that a Mexican journalist was murdered just one day after an attempted request for the location of his device was made from a European-based surveillance vendor. No doubt numerous other acts of malfeasance are buried in the millions of surveillance attempts we and others have tracked.
What to do? Frankly, there’s little you can do as a user to protect yourself from this type of geolocation tracking unless you don’t want to use a personal device to communicate when you are outside the boundary of your home network, considering that the attacks happen at the network level. Solutions will require a transformative shift in the enforcement of security policies and operational controls among telecommunications operators across the globe. Why hasn’t that happened?
Although some, like Sen. Ron Wyden (D-Ore.), have raised alarms about these risks for years, regulators in the U.S. and elsewhere have failed to address the root causes. Certain agencies in the United States should be doing more—like the Federal Communications Commission (FCC) and the Cybersecurity and Infrastructure Security Agency (CISA). They are aware of the risks but have not taken meaningful steps to address them. Their efforts have been limited to issuing recommendations and guidelines for best practices, which clearly are not being implemented. The same generally holds true for agencies in other countries.
On the industry side, international industry working groups, such as the Global System for Mobile Communications Association’s (GSMA’s) Fraud & Security Group, have issued numerous guidelines on best practices, as have the 3rd Generation Partnership Project and the International Telecommunication Union, so the risks are widely communicated to industry members. But the GSMA’s guidelines are oriented to a technical audience and comprise voluntary codes without the backing of government regulations, leaving it largely to the discretion of individual firms to implement. Part of the failure might be attributable to a still widely held assumption that light-touch regulations are best to avoid stifling innovation in the highly competitive telecommunications space. But that approach clearly no longer suffices when the severe security risks around an issue such as this persist unresolved for years. Fortunately, some regulators are beginning to move away from this hands-off approach.
The lack of public data on telecommunications attacks conceals the nature and scale of the security disaster. Where the cybersecurity industry frequently reveals attacks from adversary Advanced Persistent Threat groups, the millions of attacks from surveillance actors are kept hidden from public view. Perhaps there is a concern that the stakes are simply too high in disclosing information where the public may lose trust in telecommunications networks, or maybe that the vendors who sell network security firewalls may upset their mobile operator customers by publicizing the attacks. Either way, the lack of transparency that isolates telecommunications attacks from the mainstream cybersecurity industry places this squeaky wheel in a soundproof room.
Part of the failure may also be due to some law enforcement and security agencies actually benefiting from the status quo. After all, this signaling vulnerability yields substantial actionable intelligence on targets and their movements that is no doubt extremely valuable to those agencies. Firms selling access to signaling protocols profit handsomely, while government law enforcement and intelligence collect location data: a “win-win.” However, a collective cyber insecurity for many, many people at the most fundamental level should not be allowed to persist simply because it reaps a narrow national security and commercial benefit (which gives firms additional resources to undermine privacy and security).
The time is long overdue for regulators to finally step in and do more than make recommendations. In the United States, for example, the CISA should issue what’s known as a binding operational directive (BOD) to telecommunications firms—a legally binding measure that mandates specific actions—requiring firms to follow security recommendations. Part of that BOD could involve the requirement for telecommunications firms to commission independent compliance audits of their systems to ensure they are following best practices. The BOD could compel firms to then publish high-level summaries of those audits so that performance among them is publicly comparable. The FCC should impose penalties, fines, or other enforcement actions on companies that fail to comply with security regulations and standards, thus punishing mobile industry participants that prioritize revenues over protecting their users against such malicious activities.
Surveillance vendors providing geolocation data to authoritarian governments and regimes that engage in transnational repression should be placed on sanctions lists by the U.S. Bureau of Commerce. President Biden could issue an executive order—as a supplement to a recent order he signed to prohibit use of commercial spyware that jeopardizes national security and human rights—to forbid U.S. federal agencies from procuring geolocation services from surveillance vendors whose services create national security risks or who sell to regimes that violate human rights.
The U.S. could then build on these initiatives to coordinate a comprehensive international response to the problem, similar to a recent U.S.-backed 11-country commitment to deal with harms related to mercenary spyware. Canada is in the midst of a legislative debate over Bill C-26, which proposes comprehensive reform of telecommunications regulation. And the U.K. and France have signaled a desire to deal with a broader set of surveillance risks beyond mercenary spyware. The opportunity is ripe for the U.S. and its partners. Momentum could develop quickly around a collective approach to what is clearly a long-standing global insecurity.
The need to take action on this problem is long overdue. Surveillance-enabled transnational repression is spreading fast, exacerbating the associated international security harms. Meanwhile, the next time you step off that plane in a foreign country and boot up your device, take a moment to contemplate who might be interested in your whereabouts.
–


