
Chaos appears to reign at British Airways, where hackers stole the details of around 380,000 customer bookings. There have been some poor responses to cyber attacks on major companies in the past, but the airline’s actions in this case could be one of weakest in recent history. Part of this may be because companies are now required by the EU to report cyber attacks within 72 hours, and because information may still be being withheld due to ongoing criminal investigation.
After the company experienced power issues within its IT systems in May 2018, you would think that BA would now have plans in place to respond to computer incidents more quickly and coherently. Yet this latest hack appears to show a catalogue of missed opportunities.
First, the hack looks to have lasted for more than two weeks, affecting bookings made between August 21 and September 5. Although this means that not all BA customers are at risk – just those who made bookings during that period – it’s also not yet clear exactly who has been negatively affected and whether they will lose money as a result.
When the hack was finally discovered, BA didn’t initially provide enough coherent and robust information on the actual scope of the data taken. The company’s main statement about the hack defined the data that was not included – passport and travel details – but didn’t spell out that bank card details were involved, instead advising customers to contact their banks. This seems like trying to put a positive spin on very bad news, and means that the potential theft of what customers are most worried about – their card details – was not highlighted.
In the frequently asked questions section of the statement’s web page, it stated that: “Names, addresses, and all bank card details were all at risk.” But this didn’t give the actual details of the hack, such as whether the CVV (card verification value) security codes found on the back of cards were revealed, although BA later provided this info to the media. To not reveal if the bank details were encrypted or not, leaves too many questions still be to answered.
To be on the safe side, BA is advising all affected customers to cancel their cards. This initially led to clogged bank phone lines due to the sheer number of affected customers. Unfortunately, at present, it is not clear exactly who has actually been negatively affected. Several customers have already reported fraud on their cards.
The knee-jerk nature of the reaction was probably due to the EU’s new general data protection regulation (GDPR) that says data breaches of this kind must be reported within 72 hours of discovery.
BA’s CEO, Alex Cruz, told the BBC that the company discovered the hack on Wednesday evening and had contacted all affected customers by Thursday night. “The first thing was to find out if it was something serious and who it affected or not. The moment that actual customer data had been compromised, that’s when we began immediate communication to our customers,” he said.
He added: “We are committed to working with any customer who may have been financially affected by this attack, and we will compensate them for any financial hardship that they may have suffered.”
We should be grateful that, thanks to GDPR, the incident was at least made public quickly. Credit reporting agency Equifax took three months to report its data breach in 2017, during which time executives sold shares in the company, although an internal investigation cleared them of any insider or inappropriate trading, saying they had been unaware of the incident when they made the trades.
Dido Harding, the CEO of telecom firm TalkTalk, provided one of the best examples of how not to respond to a data breach. After the company was hacked in 2015, Harding appeared on TV suggesting customers should trust emails from TalkTalk addresses and which contained links through to the TalkTalk website. These are now understood to be standard techniques used by scammers to convince customers their emails are genuine.
Long-term impact
The maximum fine for a company data breach under GDPR is 4% of worldwide turnover. In 2017, BA’s turnover was over £12 billion, so if the company was hit with such a fine it could be over £480m, although the EU has yet to make any indication of whether the hack could lead to a fine. BA has already offered compensation for customers affected by the incident, which may reach significant amounts especially as many customers who BA alerted of the incident weren’t told whether their card details had actually been stolen.
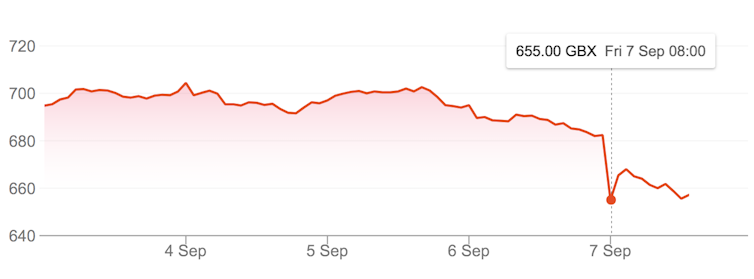
As in other examples of commercial data breaches, the initial reporting has hit the company’s share price. The market value of BA’s parent group – International Consolidated Airlines Group – was initially dented by 3.8%. But it is possibly the effect on customer trust that will have the most damage.
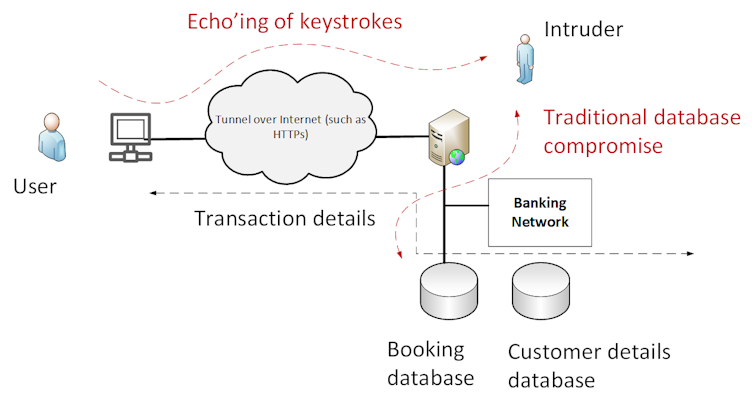
At present, few details have been released around the method of the hack. So it may involve traditional hacking methods of capturing data from a database. But if it involved capturing details of which keys users pressed on their keyboard, it would shake the foundation of our digital financial infrastructure to its core.
If there’s one thing that this hack shows, it is that we live in an extremely fragile digital world and where hacks can go undetected for some time. So we need to build financial transfer systems that integrate encryption at every single step of the process.![]()
Bill Buchanan, Head, The Cyber Academy, Edinburgh Napier University
This article is republished from The Conversation under a Creative Commons license. Read the original article.


